According to a report published by the Citizen Lab Iranian hackers
have elaborated a sophisticated phishing scheme to takeover Gmail
accounts.
According to a report
published by the Citizen Lab at the University of Toronto’s Munk School
of Global Affairs, Iranian hackers have elaborated a sophisticated
phishing scheme to circumvent security measures that defend Gmail
accounts.
The attack scheme is not new, it was used by hackers in targeted attacks on financial institutions in the past.
The Iranian hackers used phone and email to bypass Google’s two-factor authentication system and take over the victim’s Gmail account.
“This report describes an elaborate phishing campaign against
targets in Iran’s diaspora, and at least one Western activist. The
ongoing attacks attempt to circumvent the extra protections conferred by
two-factor authentication in Gmail, and rely heavily on phone-call
based phishing and “real time” login attempts by the attackers. Most of
the attacks begin with a phone call from a UK phone number, with
attackers speaking in either English or Farsi.” states the authors of
the report.
“It may be that, as a growing number of potential targets have
begun using two-factor authentication on their email accounts out of a
concern for their security, politically motivated attackers are
borrowing from a playbook that financial criminals have written over the
past decade,” state the authors of the report.
The attacks appear to be politically motivated, according
to the senior research fellow at the Citizen Lab, John Scott-Railton,
the list of targets includes a director at the Electronic Frontier
Foundation and Iranian activists.
According to security researchers, the Iranian government has increased its cyber capabilities
in a significant way in the last years, for this reason US intelligence
consider the country one of the most dangerous threats alongside with Russia, China and North Korea.
According to the research firm Small Media,
Iran increased cyber-security spending 12-fold since President Hassan
Rouhani gained power in 2013. I suggest you to give a look to the report released
by experts at Small Media. Vowing to ramp up the country’s cyber
capabilities, Rouhani has given the Islamic Revolutionary Guard Corps
(IRGC) an annual cybersecurity budget of roughly $19.8 million.
The recently observed attacks on Gmail accounts start with text
messages that pretend to be sent from Google. The messages warn users
that of unauthorized access to their Gmail accounts.

Then the attackers would send a fake “password-reset” email that
redirect victims to bogus “password reset page,” in reality the password
reset pages are used to collect the victim’s password.
The attack is called “real time” attack, it attempts to phish
both the user password and the 2FA one-time code used by Google. The
reset pages simulate the Gmail 2-step login process to the victim. The
attacker uses the victim’s input, to login in real time to Gmail. The
attacker’s login attempt triggers Google to send a genuine 2FA code to
the victim, which inserts it in the fraudulent page too. At this point,
the attack bypasses the 2FA implemented by Google.
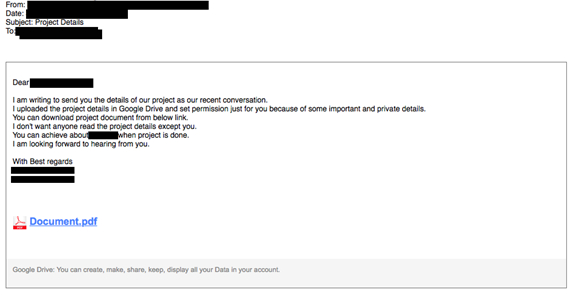
The attackers also use the phone to carry out the attack, in this
second attack scenario the victims receive a phone call regarding a fake
business proposal. The proposal would be sent to the target’s Gmail
account with a fake Google Drive link that would display victims a bogus
Gmail login page implementing a classic phishing scheme.
“Entering text into the login page and clicking on “View Document” yields a fake 2FA authentication page.”
In some attacks, the attackers tried to deceive victims by pretending to Reuters journalists who wanted to arrange an interview.
To mitigate the risk of exposure to such attacks I always suggest to
enable two-factor authentication for every online service that
implements it.
Experts suggest that an easy way to discover the fake password reset pages is to check the URL searching for the https://
prefix, unfortunately I remind you that this isn’t a complete defense
against phishing attacks because this kind of offensive is also
exploiting HTTPs connections.

